Came across this issue when an un-answered DUO push takes down AAA servers on ASA into a failed state essentially preventing everyone from VPNing in.
This site is maintained by Duo Security.We do not collect or store passwords. Login pages of other systems are for demonstration purposes only. Logging In With the Cisco AnyConnect Client. Depending on how your company configured Duo authentication, you may or may not see a “Passcode” field when using the Cisco AnyConnect client. Single Password with Automatic Push. If AnyConnect only prompts for a password, like so. Duo integrates with your Cisco ASA or Firepower VPN to add two-factor authentication to AnyConnect logins. Duo can add two-factor authentication to ASA and Firepower VPN connections in a variety of ways. Learn more about these configurations and choose the best option for your organization. Cisco ASA with AnyConnect.
Duo Cisco Anyconnect
Design was similar to this post. In short un-answered DUO push on DUO proxy would cause ISE “Radius request dropped” log message due to “11353 No more external Radius servers” which in turn would cause ASA to fail AAA radius-servers configured for VPN user authentication.
After reviewing configuration and going through multiple posts on the web I came across a similar issue (which pointed to timers) but it still did not give me the answer I was looking for so I turned to packet capture to find more clues.
First, I knew that an un-answered push has to eventually generate Access-Reject from the DUO proxy to ISE. DUO logs are verbose enough to spot “Login timed out” and Access-Reject.
Cisco Anyconnect Download Windows 10
Next, I did a packet capture on ISE to confirm Access-Reject was received and forwarded to ASA. To follow the logic below ASA IP is .4, ISE is .57, DUO proxy is .30.
So, looking at the capture below I see ASA sending Access-Request to ISE(#210), ISE to DUO(#211). Then due to an un-answered push, we’ve duplicate requests/retries and finally, DUO responds with Access-Reject(#1618) to ISE but ISE is silent and nothing is sent back to ASA. This explained why ASA Radius servers were going into a failed state. ASA kept on re-requesting an answer until the server was marked as failed (that’s when Login failed message is displayed on Anyconnect client) …. but I still did not know why ISE was not sending Access-Reject back to ASA.
I’ve tested this setup on ISE 2.7p2 and then on 2.4p9-11 to rule out any bugs and still got the same behavior. So this brought me back to reviewing configuration and taking a closer look at the timers. I was looking for clues and found one here. Based on the DUO article ISE external Radius Server Timeout had to be set to 65 seconds (by default it is 5).
Cisco Anyconnect Duo Login Failed
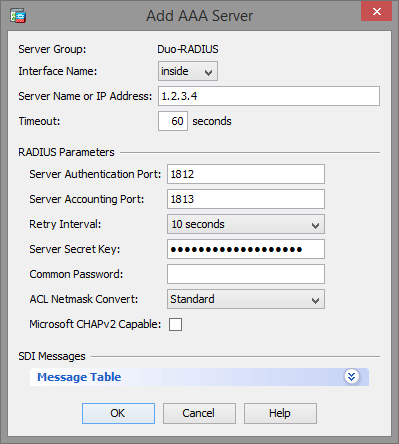
Looking at ASA configuration I see my Radius server timeout is set to 60.
aaa-server ISE (inside) host <IP>
timeout 60
key *****
After updating timeouts I did another capture. To follow the below logic ASA IP is .4, ISE is .22, DUO proxy is .30. We see the same behavior up until DUO returns Access-Reject to ISE (#3237) and now we see ISE returns Access-Reject to ASA (#3239).

This is because ISE did not mark DUO as a dead server before ASA marked ISE as unavailable (65 > 60) so when ISE received reject from DUO it forwarded it to the ASA.
The issue was resolved.

Comments are closed.